Incident Response and Management
- Home
- Incident Response and Management
Service
Incident Response and Management
Our Incident Response and Management services provide rapid, expert support to detect, contain, and remediate cybersecurity incidents. We help minimize damage and downtime by quickly identifying threats, analyzing their impact, and implementing effective containment and recovery strategies. Our proactive approach ensures your organization is prepared to respond efficiently to any security breach or cyber attack.
With comprehensive planning, real-time monitoring, and thorough post-incident analysis, we not only address immediate threats but also strengthen your defenses to prevent future incidents. Trust us to safeguard your critical assets and maintain business continuity during challenging security events.
Incident Response Planning
Incident Response Planning involves creating structured procedures and protocols to effectively detect, respond to, and recover from cybersecurity incidents. This proactive approach helps minimize damage, reduce recovery time, and ensure business continuity. A well-developed incident response plan equips teams to act swiftly and decisively during security breaches.

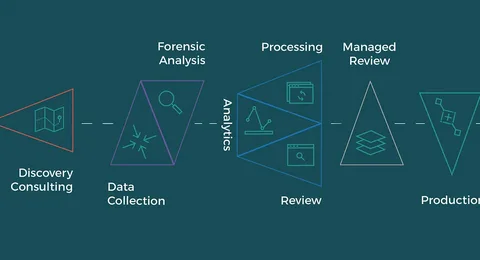
Forensic Analysis
Forensic Analysis is the process of investigating cybersecurity incidents to uncover how breaches occurred and what systems were affected. It involves collecting, analyzing, and preserving digital evidence to support legal actions and internal reviews. This helps organizations identify vulnerabilities, understand attacker behavior, and prevent future incidents. Accurate forensic analysis is essential for timely recovery and strengthening overall security posture.
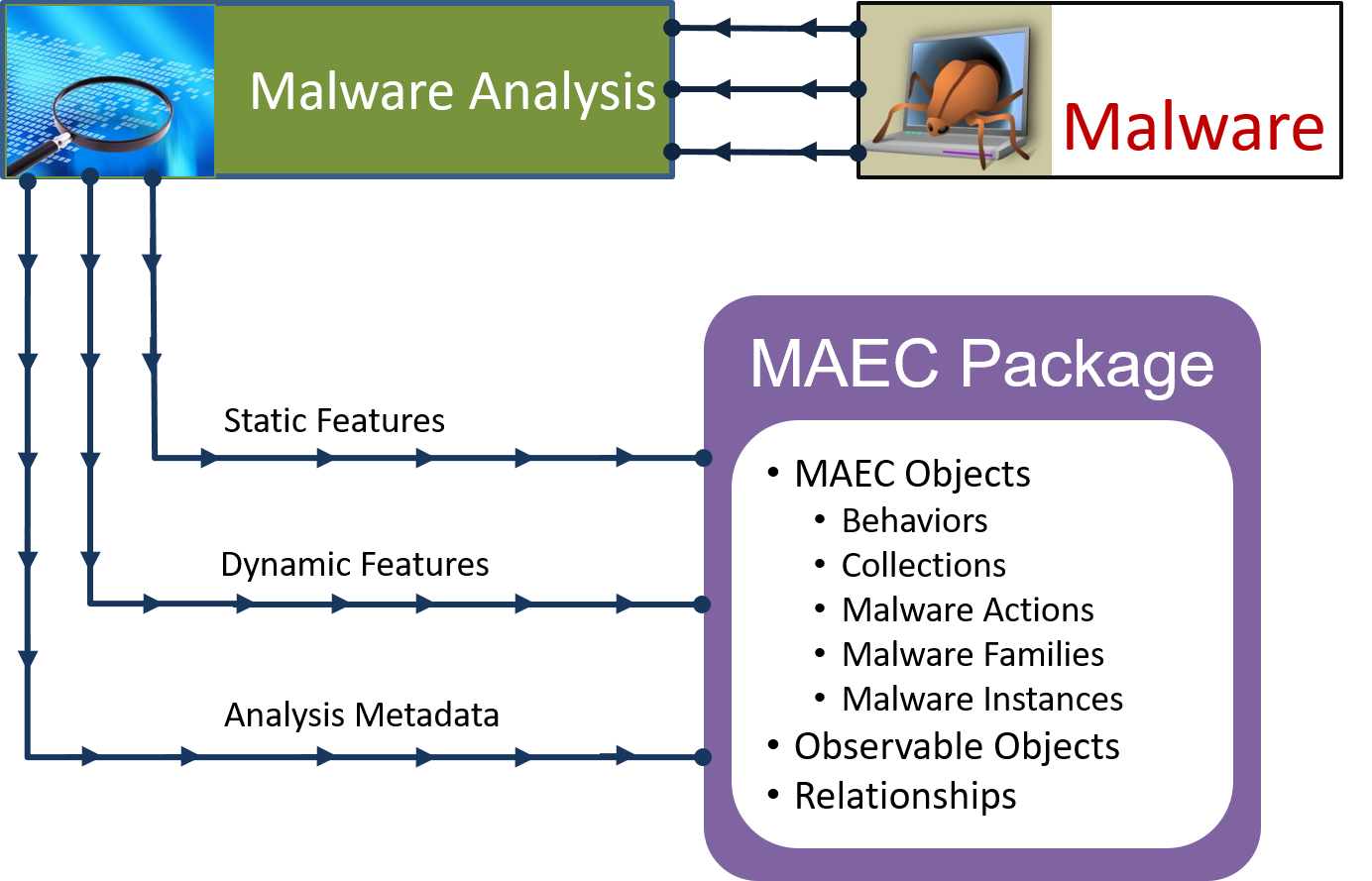
Malware Analysis
Malware Analysis is the process of examining malicious code to uncover its functionality, origin, and potential impact on systems. It involves both static and dynamic analysis techniques to observe the behavior of malware in controlled environments. This helps security professionals identify indicators of compromise (IOCs), understand the attack vectors used, and develop tailored detection and prevention strategies. Malware analysis is critical for incident response, threat intelligence, and improving defensive capabilities. By understanding how malware operates, organizations can better protect their networks and respond effectively to cyber threats.

Data Breach Investigation
Data Breach Investigation involves thoroughly analyzing security incidents to determine how a breach occurred, what data was accessed or stolen, and the overall impact on the organization. The process includes identifying entry points, tracing attacker activity, and evaluating the extent of data exposure. Investigators work to contain the breach, mitigate ongoing risks, and support legal, regulatory, and notification requirements. A well-conducted breach investigation helps strengthen defenses and prevent future incidents.
Business Continuity and Disaster Recovery (BC/DR)
Business Continuity and Disaster Recovery (BC/DR) focuses on maintaining essential business operations during and after a cyber incident or any disruptive event. It involves strategic planning, risk assessments, and the implementation of recovery protocols to minimize downtime and data loss. BC/DR ensures that critical systems remain operational, employees are informed and equipped to respond, and recovery processes are swift and structured. By proactively preparing for emergencies, organizations can protect assets, maintain customer trust, and ensure long-term resilience.

Discover Solutions
See what Discipline can do for your organization
At Discipline, we place your business needs first. Our success is your success. To help you achieve your goals, we invest in our people and resources, so that they can help bring new business models and innovative ideas to your business and work environment. Our engagement model is flexible, giving clients the best access to services while meeting time and budget requirements.
Contact Us
Ready to Elevate Your IT Strategy?
Connect with us to explore how our innovative services can address your unique challenges. Our experts are ready to guide you with personalized support and strategic solutions. Let’s build a secure and future-ready digital environment together.



