Security Monitoring and Operations
- Home
- Security Monitoring and Operations
Service
Security Monitoring and Operations
Our Security Monitoring and Operations services provide continuous, real-time surveillance of your IT environment to detect and respond to threats promptly. By leveraging advanced tools and expert analysis, we ensure your systems are protected around the clock from cyber attacks, unauthorized access, and suspicious activities.
We manage security alerts, perform threat hunting, and maintain incident response readiness to keep your organization secure and compliant. With proactive monitoring and operational support, we help you stay ahead of evolving cyber risks and maintain a strong security posture.
Managed Security Services (MSS)
Managed Security Services (MSS) involve outsourcing your organization’s cybersecurity operations to a team of dedicated experts. These services typically include 24/7 monitoring, threat detection and response, vulnerability management, and compliance support. MSS providers deliver cost-effective, scalable protection, allowing businesses to stay ahead of evolving threats while focusing on core operations.


24/7 Security Operations Center (SOC) Monitoring
24/7 Security Operations Center (SOC) Monitoring provides round-the-clock surveillance of IT environments to detect and respond to security threats in real time. This continuous vigilance ensures rapid identification of potential incidents, minimizing risk and maintaining the integrity and availability of critical systems. With expert analysts constantly monitoring, your organization stays protected against evolving cyber threats.
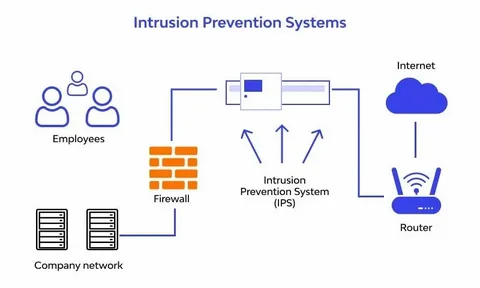
Intrusion Detection and Prevention Systems (IDPS)
Intrusion Detection and Prevention Systems (IDPS) monitor network and system activities to identify potential security threats in real time. They not only detect malicious behavior but also actively block and prevent attacks before they can cause harm. By continuously analyzing traffic and system events, IDPS helps safeguard critical infrastructure, ensuring immediate response to vulnerabilities and reducing the risk of data breaches or downtime. This technology is essential for maintaining a strong and proactive cybersecurity defense.

Log Management
Log Management involves the systematic collection, storage, and analysis of security logs from various systems and devices. By monitoring these logs, organizations can detect unusual activities or anomalies that may indicate security threats or breaches. Effective log management helps in timely incident detection, forensic investigations, and compliance with regulatory requirements, enhancing overall security posture.
Discover Solutions
See what Discipline can do for your organization
At Discipline, we place your business needs first. Our success is your success. To help you achieve your goals, we invest in our people and resources, so that they can help bring new business models and innovative ideas to your business and work environment. Our engagement model is flexible, giving clients the best access to services while meeting time and budget requirements.
Contact Us
Ready to Elevate Your IT Strategy?
Connect with us to explore how our innovative services can address your unique challenges. Our experts are ready to guide you with personalized support and strategic solutions. Let’s build a secure and future-ready digital environment together.



