Enterprise Security Architecture
- Home
- Enterprise Security Architecture
Service
Enterprise Security Architecture
Enterprise Security Architecture is the strategic framework that aligns an organization’s security measures with its business objectives and IT infrastructure. It provides a structured approach to designing, implementing, and managing security controls across systems, networks, and applications.
By integrating security at every level—from data flow to access control—it ensures a resilient environment that supports scalability, regulatory compliance, and continuous risk mitigation in today’s complex threat landscape.
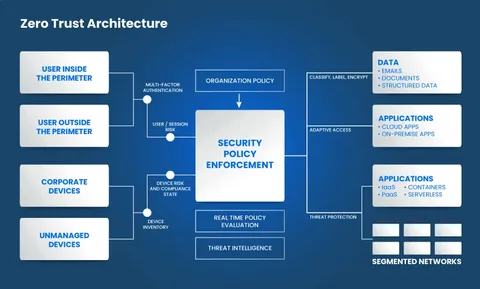
Zero Trust Architecture Implementation
Zero Trust Architecture Implementation involves creating a perimeter-less security framework that continuously verifies every user and device based on identity and context. This approach minimizes risk by enforcing strict access controls, assuming no implicit trust inside or outside the network. It enhances protection against modern cyber threats by ensuring that only authenticated and authorized entities can access critical resources.

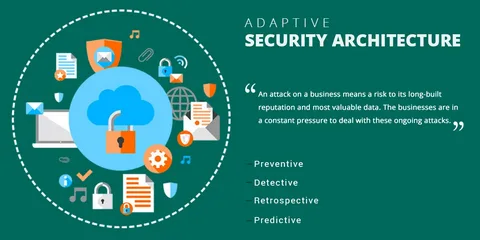
Security Architecture Review
Security Architecture Review involves evaluating your existing security framework to identify gaps and vulnerabilities. It also includes designing robust, scalable, and secure architectures tailored to your organization’s needs, ensuring stronger protection against evolving cyber threats and compliance with industry standards.
Network Security Architecture
Network Security Architecture centers on designing and deploying secure network infrastructures that protect data transmission and block unauthorized access. It builds resilient, scalable systems using multiple layers of defense to guard against cyber threats. This approach ensures continuous, reliable connectivity while maintaining the integrity and confidentiality of network communications.
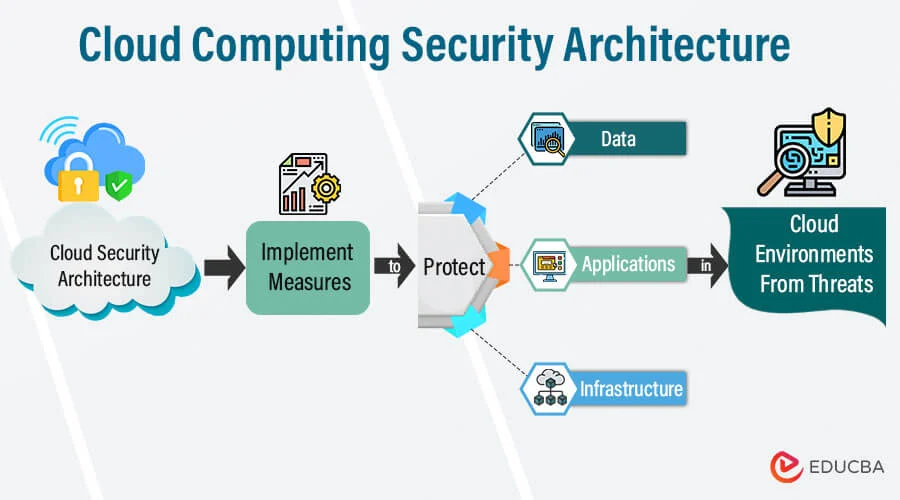
Cloud Security Architecture
Cloud Security Architecture involves implementing strong security controls across major cloud platforms such as AWS, Azure, GCP, and hybrid environments. It focuses on protecting data, managing access, and preventing threats while maintaining compliance with industry standards. This architecture supports secure, scalable, and efficient cloud operations. By continuously monitoring and adapting to emerging risks, it ensures the integrity and availability of cloud resources.
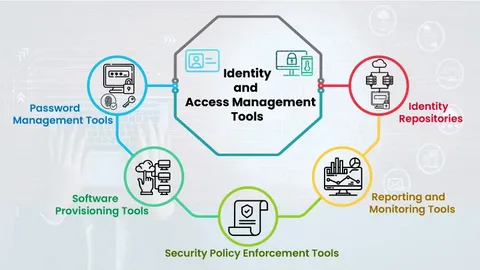
Identity and Access Management (IAM)
Identity and Access Management (IAM) involves implementing robust systems to manage user identities and control access to critical resources. It ensures that the right individuals have appropriate access while preventing unauthorized users from gaining entry. By enforcing strong authentication and authorization policies, IAM helps protect sensitive data and supports regulatory compliance. Effective IAM reduces security risks and improves operational efficiency across the organization.
Data Security Architecture
Data Security Architecture focuses on designing secure frameworks for data processing, storage, and transmission. It ensures that sensitive information is protected against unauthorized access, breaches, and data loss throughout its lifecycle. By implementing encryption, access controls, and monitoring, this architecture safeguards data integrity and confidentiality. It plays a critical role in meeting compliance requirements and supporting overall organizational security.
Discover Solutions
See what Discipline can do for your organization
At Discipline, we place your business needs first. Our success is your success. To help you achieve your goals, we invest in our people and resources, so that they can help bring new business models and innovative ideas to your business and work environment. Our engagement model is flexible, giving clients the best access to services while meeting time and budget requirements.
Contact Us
Ready to Elevate Your IT Strategy?
Connect with us to explore how our innovative services can address your unique challenges. Our experts are ready to guide you with personalized support and strategic solutions. Let’s build a secure and future-ready digital environment together.



